Kusari Platform
Secure every link in your software supply chain
Look beneath the surface for full context into every level of your open source code and its dependencies, without the noise. Know your software, fix what matters, and prove you’re in control.


Use Cases
Move fast with confidence
Fix what matters
Rank risks by severity, breadth, and exploitability. Then quickly see the effort to fix, root cause, and clear remediation instructions.
See HowEnforce policy
Make your developers the first line of defense with security guardrails in the tools they already use. Zero tolerance policy is now a possibility.
Explore InspectorProve trust
Generate real-time SBOMs by time, package, or vulnerability lists so you can maintain compliance and ship code fast at the speed of development
See How
87% reduction of vulnerabilities in 30 days for software security company
Read Case StudyFeatures
Skip the noise with deeper visibility
Get an actionable map of what to fix and where, in seconds.
Book a DemoKusari Score
Know what to fix first
Not every vulnerability is an immediate risk. Check to see if the vulnerable code is even being used, if it’s exposed, and if it’s actually dangerous, so you only spend time fixing things that matter.
How it Works
Effort to fix
Neutralize key threats fast
The size of a fix makes a big difference. Know whether you’re updating a library that is going to be a one-line change or if it will break five other systems, so you can plan realistically and knock out the easy stuff fast.
How it’s Calculated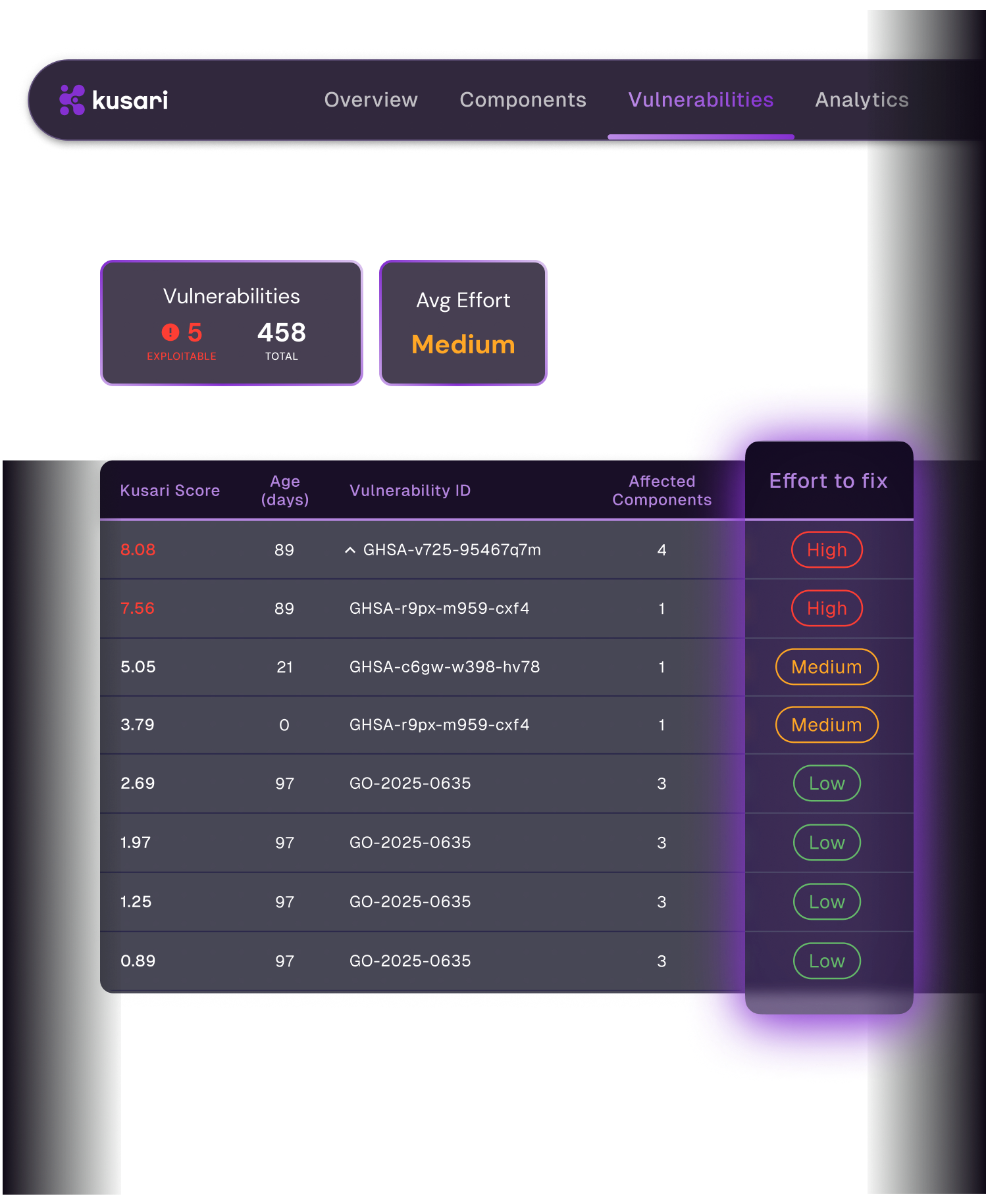
TRANSITIVE DEPENDENCIES
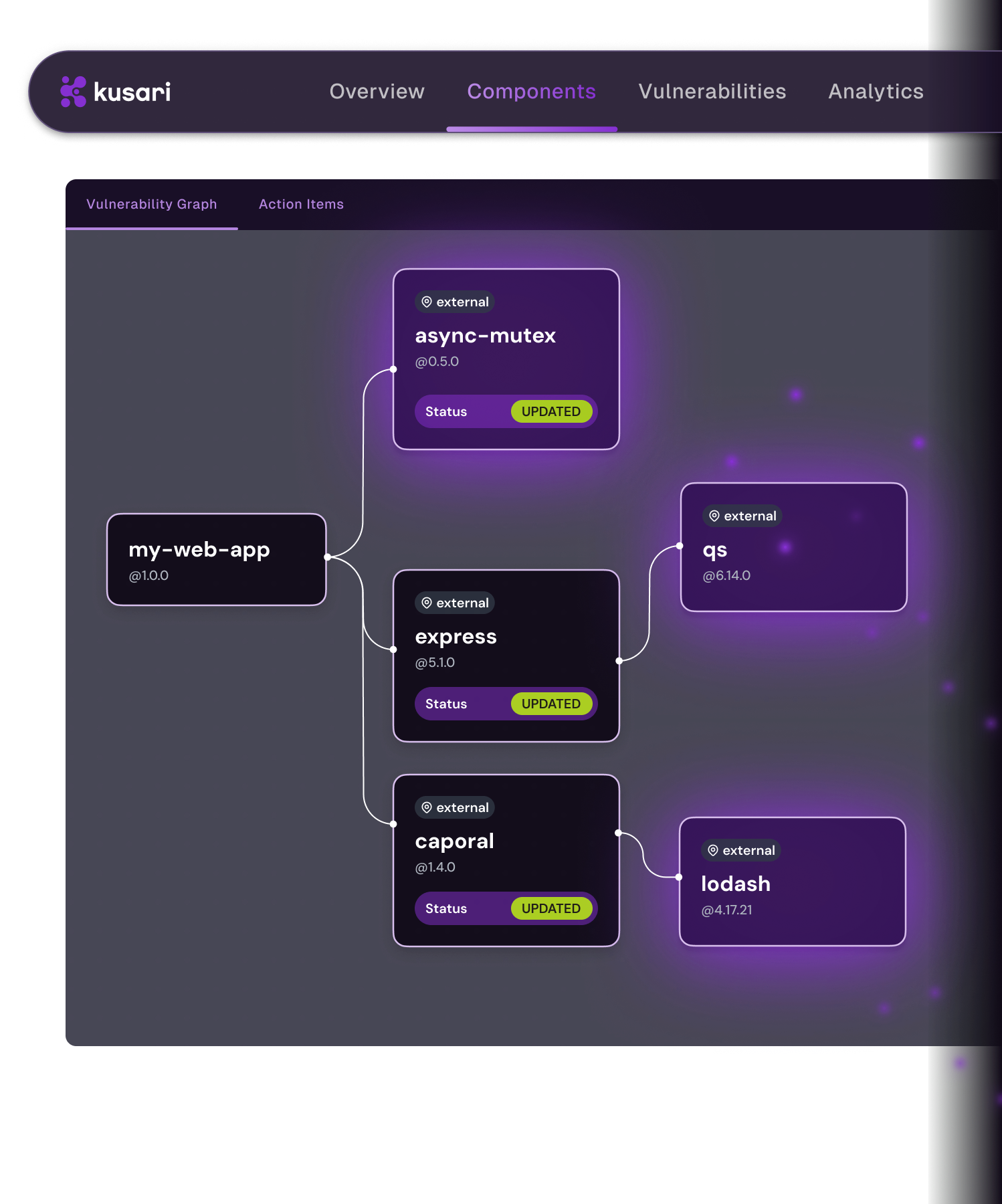
Fix threats at the root
What fixes might introduce new vulns? Forget the flat list of noisy vulnerabilities. Identify which component to fix at the top of a dependency chain and get clear remediation instructions. Fix it there and let that automatically neutralize any vulnerabilities down the chain, without introducing any new ones.
Explore Transitive Dependencies

RISK MANAGEMENT
Be audit-ready every day
Prove your software is safe in seconds. Generate SBOMs and see what’s in your code, what was fixed, what’s still being worked on, and who touched what. Trace any issues back to the source between every version, change, component at every release.
Learn More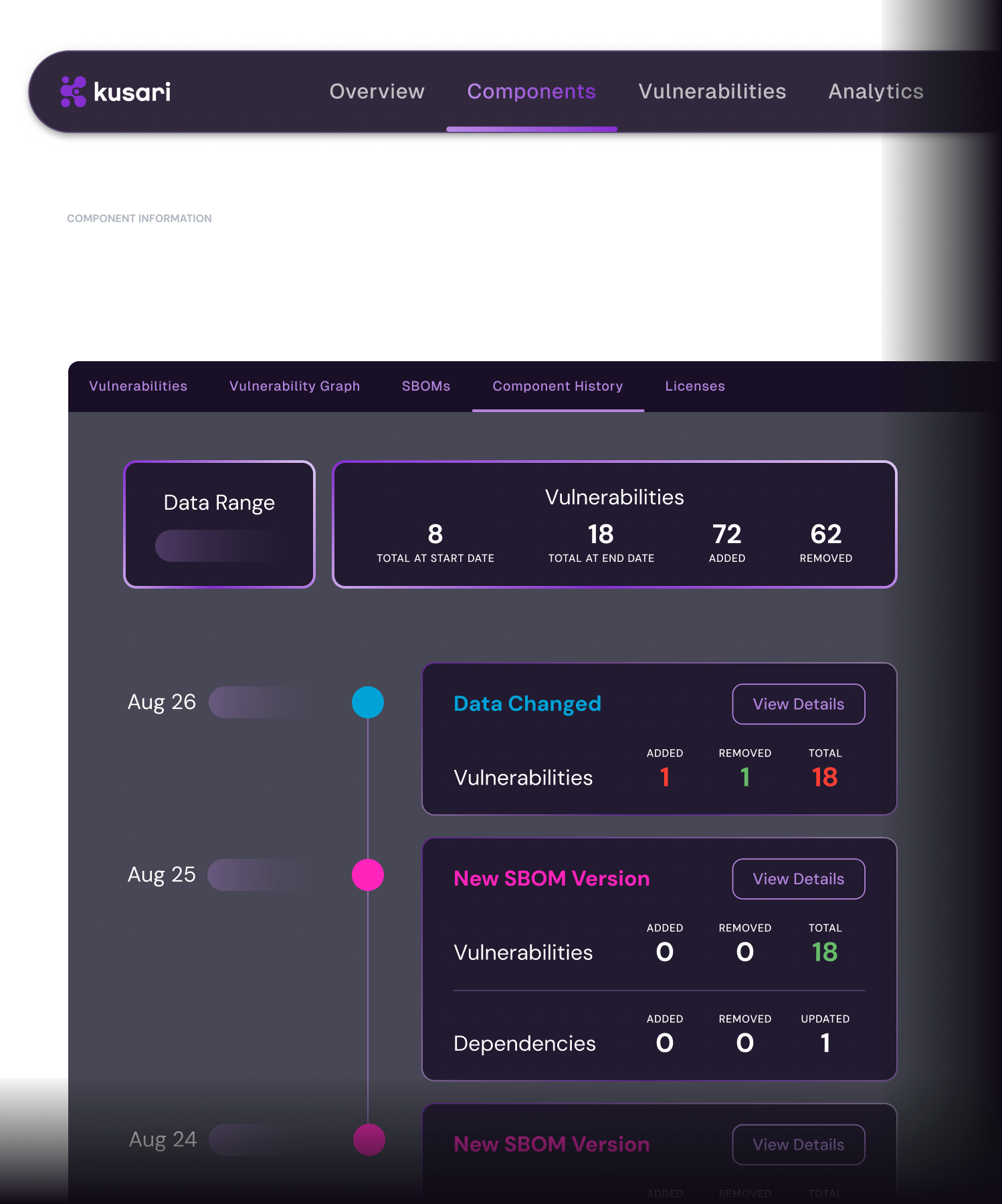
Scale security for the whole team
Organization-wide visibility
Automatically aggregate insights across all connected projects and repositories.
Internal package tracking
Detect and map internal packages, showing where they’re used, by whom, and whether they’ve been reviewed.
Provenance and lineage
Visualize the history and movement of packages across projects, like Git meets SBOMs.
Risk correlation across projects
Identify shared risks across microservices, like a vulnerable dependency used in 5 other apps.
Role-based access & collaboration
Invite engineering, security, and compliance stakeholders into shared workspaces.

Central policy enforcement
Define org-wide rules, like block GPL-licensed packages or 2 reviewers being required for critical deployments.
CI/CD and registry integration
Pull in data from builds, artifacts, and deployments for end-to-end supply chain visibility.
Dashboards and digest reports
Get weekly reports, alert routing, and high-level overviews for security teams and leadership.

Industries
For regulated industries

Protect patient data and comply with industry regulations. Secure every software dependency powering medical devices and other clinical systems.
Security Lead
Medical Device Company

Prevent malicious code from slipping into your mission-critical systems. Bring transparency and trust to every layer of your defense software stack.
Security Lead
Medical Device Company

Shield operational tech and infrastructure from online threats. Increase visibility and control with Kusari over the software components powering your utilities.
Security Lead
Medical Device Company

Protect your financial systems from the code up. Kusari secures your software supply chain to keep transaction and customer data safe.
Security Lead
Medical Device Company

We built Kusari to protect customers, but decided to test it on ourselves first. In 30 days, we cut our vulnerabilities by 87%, and our delivery pipeline is stronger than ever.
Tim Miller
CEO at Kusari

Security that protects beneath the surface
Get a Demo











