XML Security
XML security represents the collection of practices, protocols, and technologies designed to protect Extensible Markup Language (XML) data and processes from unauthorized access, manipulation, and exploitation. For DevSecOps leaders managing enterprise applications, understanding XML Security becomes critical when dealing with configuration files, API communications, and data interchange formats that organizations rely upon daily. The persistent use of XML across legacy systems and modern applications creates a complex attack surface that requires dedicated security measures to prevent vulnerabilities from compromising your software supply chain.
What is XML Security in DevSecOps?
XML Security encompasses multiple dimensions of protection for XML-based systems and data. The framework addresses authentication, authorization, data integrity, confidentiality, and non-repudiation requirements specific to XML documents and processing mechanisms. Unlike generic security approaches, XML Security accounts for the unique structural characteristics of markup languages and the specific threats that target these systems.
Organizations implementing DevSecOps practices must recognize that XML serves as both a data format and an execution vehicle in many scenarios. Configuration files, build manifests, dependency declarations, and API payloads frequently use XML structures. This dual nature means that compromised XML data can affect both information confidentiality and system behavior, making XML Security a supply chain security concern rather than just a data protection issue.
Core Components of XML Security
The discipline encompasses several standardized technologies and best practices:
- XML Signature (XMLDSig): Provides methods for creating and verifying digital signatures on XML documents or portions thereof, ensuring data integrity and authenticity
- XML Encryption (XMLEnc): Enables encryption of entire XML documents or specific elements, protecting sensitive data from unauthorized disclosure
- XML Access Control: Implements authorization mechanisms to control who can access, modify, or process specific XML resources
- Secure XML Processing: Addresses vulnerabilities in XML parsers and processors to prevent injection attacks and resource exhaustion
- XML Key Management: Handles cryptographic keys used in signing and encryption operations
Common XML Security Threats Facing Development Teams
DevSecOps teams face numerous XML-specific threats that differ from traditional application security concerns. Understanding these attack vectors helps teams prioritize security controls and implement effective defenses.
XML External Entity (XXE) Attacks
XXE attacks exploit XML parsers that process external entity references without proper validation. Attackers craft malicious XML documents containing references to external resources, potentially leading to:
- Disclosure of local files from the server filesystem
- Internal network scanning and port enumeration
- Server-side request forgery (SSRF) attacks
- Denial of service through resource exhaustion
- Remote code execution in certain configurations
For teams managing containerized applications and microservices, XXE vulnerabilities in XML parsers can provide attackers with access to configuration files, secrets, and internal service endpoints. The attack surface expands when XML processing occurs in multiple services across distributed architectures.
XML Injection Vulnerabilities
XML injection attacks occur when applications incorporate untrusted input into XML documents without proper sanitization. Attackers manipulate document structure by injecting malicious markup, potentially achieving:
- Modification of application logic based on XML configuration
- Privilege escalation through altered authorization data
- Data exfiltration by manipulating query structures
- Business logic bypass through modified parameters
These vulnerabilities frequently appear in SOAP web services, configuration management systems, and applications that generate XML dynamically from user input. The risk increases when XML structures control security-critical functions like authentication or authorization decisions.
Billion Laughs and Entity Expansion Attacks
Resource exhaustion attacks leverage XML's entity expansion mechanism to consume excessive memory or processing resources. The "Billion Laughs" attack defines nested entities that expand exponentially, causing denial of service conditions. Teams running XML processing in shared environments or container orchestration platforms must protect against these attacks to maintain service availability for all workloads.
XPath and XQuery Injection
When applications use XPath or XQuery to retrieve data from XML documents, unsanitized input can lead to injection vulnerabilities similar to SQL injection. Attackers manipulate query logic to:
- Access unauthorized data elements
- Bypass authentication mechanisms
- Extract entire document contents
- Modify query results to alter application behavior
XML Signature Wrapping Attacks
Signature wrapping attacks exploit weaknesses in XML Signature verification implementations. Attackers manipulate signed documents by adding, moving, or duplicating elements in ways that pass signature validation but change the document's meaning. SOAP-based web services and signed configuration files are particularly vulnerable to these sophisticated attacks.
XML Security Standards and Specifications
Several industry standards govern XML Security implementations. Understanding these specifications helps teams select appropriate tools and verify that security controls meet established requirements.
XML Signature (XMLDSig)
The XML Signature specification defines XML syntax and processing rules for creating and representing digital signatures. XMLDSig supports three signature types:
- Enveloped signatures: The signature is contained within the signed content
- Enveloping signatures: The signed content is contained within the signature element
- Detached signatures: The signature exists separately from the signed content
Teams implementing XMLDSig must configure canonicalization properly to ensure consistent signature verification across different processing environments. The specification provides multiple canonicalization algorithms, each with different security properties and compatibility considerations.
XML Encryption (XMLEnc)
XML Encryption enables selective encryption of XML documents, allowing teams to protect sensitive elements while leaving other portions in plaintext. This granular approach supports use cases where partial document inspection is necessary while maintaining confidentiality for specific data fields.
The specification supports various encryption algorithms and key transport mechanisms. Teams must select algorithms appropriate for their security requirements while maintaining compatibility with partner systems and compliance frameworks.
WS-Security
WS-Security extends SOAP messaging with security capabilities including message integrity, confidentiality, and authentication. The standard builds upon XML Signature and XML Encryption to provide end-to-end security for web services communication. Organizations operating service-oriented architectures or integrating with partner systems through SOAP interfaces rely on WS-Security implementations to protect data in transit.
Security Assertion Markup Language (SAML)
SAML uses XML structures to exchange authentication and authorization data between identity providers and service providers. The standard enables single sign-on and federated identity management across organizational boundaries. Teams implementing SAML must address XML Security concerns specific to assertion handling, including signature verification, encryption of sensitive attributes, and protection against replay attacks.
Implementing XML Security in DevSecOps Pipelines
Securing XML throughout the software development lifecycle requires integrating security controls at multiple stages. DevSecOps teams should implement defense-in-depth strategies that address vulnerabilities before production deployment.
Secure XML Parser Configuration
Parser configuration represents the first line of defense against XML-based attacks. Teams should configure parsers to:
- Disable external entity processing unless explicitly required
- Limit entity expansion to prevent resource exhaustion
- Restrict DTD processing to block entity-based attacks
- Enable secure processing features provided by parser libraries
- Set resource limits for document size, element depth, and attribute counts
Different programming languages and XML libraries provide varying mechanisms for these configurations. Teams must research secure defaults for their specific technology stack and implement consistent settings across all services that process XML data.
Input Validation and Sanitization
Applications accepting XML input should validate documents against strict schemas before processing. Schema validation ensures that documents conform to expected structures and contain only permitted elements and attributes. Beyond schema validation, teams should:
- Reject documents containing unexpected entity declarations
- Validate that document size remains within acceptable limits
- Sanitize user-provided data before incorporating into XML structures
- Use parameterized approaches for XPath and XQuery operations
- Implement allowlists for permitted elements and attributes
Static Application Security Testing (SAST)
SAST tools can identify XML Security vulnerabilities in source code before deployment. Teams should configure SAST scanners to detect:
- Insecure XML parser configurations
- XML injection vulnerabilities in document generation code
- XPath injection risks in query construction
- Improper signature verification implementations
- Weak or deprecated cryptographic algorithms in encryption code
Integrating SAST into continuous integration pipelines enables teams to identify vulnerabilities early when remediation costs remain low. Automated scanning should complement manual code review for security-critical XML processing logic.
Dependency Scanning and Software Composition Analysis
XML parsing libraries frequently contain vulnerabilities that attackers can exploit. Teams must maintain awareness of security issues in dependencies and update libraries promptly when patches become available. Software composition analysis tools help teams:
- Inventory XML-related dependencies across projects
- Identify known vulnerabilities in XML libraries
- Track available updates and security patches
- Assess the risk profile of open source components
- Generate software bills of materials (SBOMs) for supply chain transparency
Runtime Application Self-Protection (RASP)
RASP solutions monitor application behavior during execution to detect and block XML attacks in real-time. These tools can identify exploitation attempts that bypass static analysis and provide defense-in-depth protection. RASP capabilities relevant to XML Security include:
- Detection of XXE exploitation attempts
- Blocking of XML injection attacks
- Prevention of resource exhaustion from entity expansion
- Monitoring of XPath query execution for injection patterns
Security Testing in CI/CD Pipelines
Automated security testing should verify XML Security controls throughout the development lifecycle. Teams can implement:
- Unit tests that verify parser configurations block known attack patterns
- Integration tests that validate end-to-end encryption and signature verification
- Fuzzing tests that supply malformed XML to identify parser vulnerabilities
- Dynamic application security testing (DAST) that probes deployed applications for XML vulnerabilities
XML Security in Software Supply Chain
XML Security intersects with software supply chain security in numerous ways. Understanding these connections helps teams implement comprehensive protection strategies.
Build and Deployment Manifests
Many build systems and deployment tools use XML formats for configuration. Maven's pom.xml files, Ant build scripts, and various deployment descriptors all represent potential attack vectors. Compromised build configurations can inject malicious dependencies, modify compilation settings, or alter deployment parameters.
Teams should treat build manifests as security-critical assets requiring:
- Version control with audit trails for all modifications
- Code review processes for configuration changes
- Signature verification to ensure manifest authenticity
- Access controls limiting who can modify build definitions
- Validation against schemas to prevent unexpected configurations
Dependency Resolution and Package Management
Package managers that use XML metadata files (such as Maven repositories) require security controls to prevent dependency confusion attacks and malicious package substitution. Teams should:
- Verify signatures on repository metadata
- Use private registries for internal dependencies
- Implement repository managers with access controls
- Monitor for suspicious dependency modifications
- Pin dependency versions to prevent unexpected updates
Configuration Management
Applications often use XML files for runtime configuration, including database connections, API endpoints, and security settings. Compromised configuration files can redirect applications to attacker-controlled resources or disable security controls. Protection strategies include:
- Encrypting sensitive values within configuration files
- Storing configurations in secure secret management systems
- Implementing integrity checks to detect tampering
- Restricting filesystem permissions on configuration files
- Using immutable infrastructure patterns where configurations are baked into container images
API Security
SOAP-based APIs and REST services that accept XML payloads require comprehensive security controls. API gateways should implement:
- Schema validation for incoming XML requests
- Rate limiting to prevent denial of service
- Request size limits to block oversized documents
- WS-Security enforcement for SOAP services
- Logging and monitoring for suspicious XML patterns
XML Security Best Practices for Enterprise Teams
Organizations implementing XML Security should adopt comprehensive practices that address technical controls, processes, and governance.
Principle of Least Privilege
Apply minimal permissions to XML processing components. Services should run with limited filesystem access, network restrictions, and resource quotas. Container security contexts and security policies should explicitly deny unnecessary capabilities that could exacerbate XML exploitation.
Defense in Depth
Layer multiple security controls to create redundant protection. Combine secure parser configuration, input validation, schema enforcement, and runtime monitoring to ensure that failures in one layer don't compromise the entire system.
Secure Defaults
Configure XML parsers and processors with security-first defaults. Disable dangerous features unless specific use cases require them, then enable those features only for the minimum necessary scope. Create reusable configuration templates that teams can apply consistently across projects.
Cryptographic Hygiene
Use strong, modern cryptographic algorithms for XML Signature and XML Encryption. Avoid deprecated algorithms like SHA-1 and MD5 for signatures, and use authenticated encryption modes like AES-GCM. Implement proper key management practices including:
- Hardware security modules (HSMs) or cloud key management services for key storage
- Regular key rotation schedules
- Separation of signing and encryption keys
- Secure key distribution mechanisms
- Key lifecycle management including creation, rotation, and destruction
Monitoring and Incident Response
Implement logging and monitoring to detect XML-based attacks. Monitor for indicators including:
- Parsing errors that may indicate exploitation attempts
- Unusual resource consumption patterns
- Failed signature verifications
- Suspicious XPath query patterns
- Unexpected external entity references
Develop incident response playbooks specifically for XML Security incidents, including procedures for investigating parser exploitation, analyzing compromised documents, and remediating affected systems.
Developer Training and Security Awareness
Educate development teams about XML Security threats and secure coding practices. Training should cover:
- Common XML vulnerabilities and exploitation techniques
- Secure parser configuration for team's technology stack
- Proper implementation of XML Signature verification
- Correct usage of XML Encryption APIs
- Security testing approaches for XML-processing code
Comparing XML Security Approaches Across Technologies
Different programming languages and frameworks provide varying levels of XML Security support. Teams should understand the strengths and limitations of their chosen technologies.
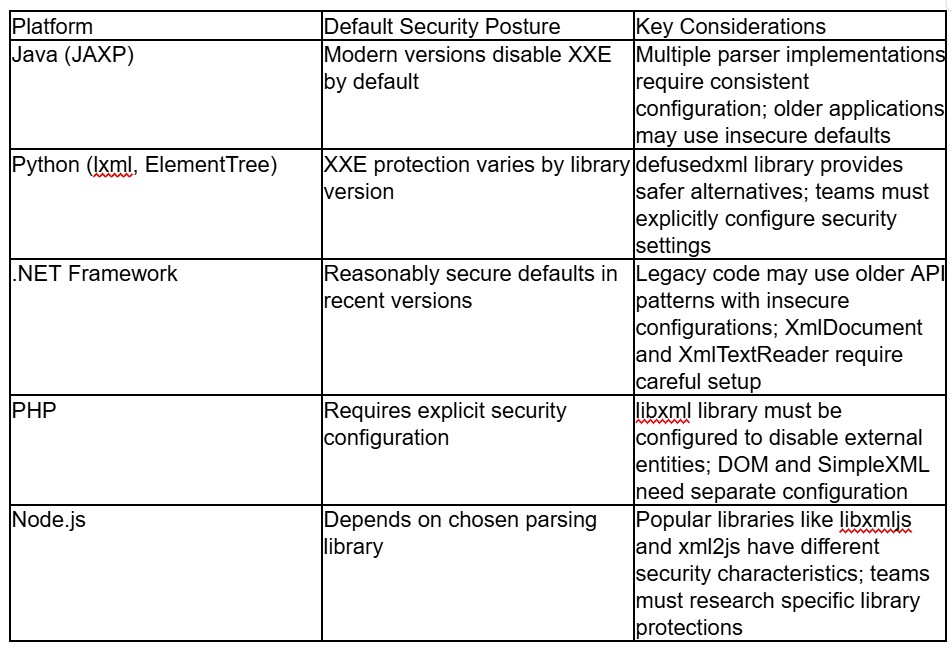
Balancing XML Security with Performance Requirements
Security controls can impact XML processing performance. Teams must find appropriate balances between protection and efficiency.
Schema Validation Overhead
Validating XML documents against schemas adds processing time. For high-throughput services, teams can:
- Cache compiled schemas to avoid repeated parsing
- Perform validation asynchronously for non-critical workflows
- Implement sampling strategies that validate a percentage of requests
- Use lightweight validation for trusted internal sources
Cryptographic Operation Costs
XML Signature creation and verification consume CPU resources. Optimization strategies include:
- Hardware acceleration for cryptographic operations
- Signature caching for repeatedly processed documents
- Selective signing of security-critical elements rather than entire documents
- Using efficient signature algorithms appropriate for threat models
Parser Selection
Different XML parsers offer varying performance characteristics. Teams should benchmark parsers for their specific workloads while ensuring selected parsers provide necessary security features. Streaming parsers (SAX-style) generally offer better performance for large documents compared to DOM-based parsers but require different programming patterns.
Regulatory Compliance and XML Security
Various compliance frameworks address XML Security requirements. Organizations subject to regulatory oversight must implement controls that satisfy applicable standards.
PCI DSS
Payment Card Industry Data Security Standard requires protection of cardholder data during transmission and storage. Organizations using XML formats for payment data must implement XML Encryption for sensitive elements and XML Signature for integrity protection. Key management requirements apply to cryptographic keys used in XML Security operations.
HIPAA
Healthcare organizations exchanging protected health information (PHI) in XML formats must implement appropriate safeguards. The Security Rule requires confidentiality, integrity, and availability controls that extend to XML-based systems. HL7 and other healthcare standards that use XML require careful security implementation.
GDPR
General Data Protection Regulation requirements for data protection by design and by default apply to XML processing systems. Organizations must implement appropriate technical measures to protect personal data, including encryption, pseudonymization, and access controls. Data minimization principles suggest encrypting only necessary XML elements rather than entire documents when selective processing is possible.
Future Trends in XML Security
While JSON and other formats have gained popularity, XML remains prevalent in enterprise environments. Several trends are shapeing XML Security's evolution.
Cloud-Native Architectures
Microservices and containerized applications require distributed XML Security controls. Service mesh technologies can provide centralized policy enforcement for XML processing, including validation, signature verification, and encryption. Teams adopting cloud-native patterns must ensure XML Security controls work effectively in ephemeral, dynamically-scaled environments.
Zero Trust Security Models
Zero trust principles apply to XML processing systems just as they do to other components. Never trust XML data based on its source network location. Always verify signatures, validate schemas, and enforce authorization policies regardless of where documents originate. Implement continuous verification rather than perimeter-based security assumptions.
Supply Chain Transparency
Software bills of materials increasingly use standardized formats like SPDX and CycloneDX, some of which support XML representations. Teams must apply XML Security principles to SBOM documents, including signature verification to ensure SBOM integrity and authenticity. Compromised SBOMs could mislead teams about their dependency profiles and security postures.
Strengthening Your Security Posture with XML Protection
Managing XML Security represents a critical component of comprehensive DevSecOps practices for teams working with enterprise applications, microservices architectures, and software supply chains. The persistence of XML across build systems, configuration management, API communications, and legacy integrations means that teams cannot ignore XML-specific threats even as newer data formats gain adoption. Organizations face sophisticated attack vectors ranging from XXE vulnerabilities to signature wrapping attacks, requiring layered defenses combining secure parser configuration, input validation, cryptographic protection, and runtime monitoring.
Teams implementing XML Security must balance protection requirements with performance needs while navigating complex compliance landscapes. The discipline extends beyond technical controls to encompass developer training, secure coding practices, and integration of security testing throughout CI/CD pipelines. Understanding the intersection between XML Security and software supply chain concerns helps teams protect build manifests, dependency metadata, and configuration files that influence system behavior and security postures.
Modern approaches incorporate XML Security into zero trust architectures, service mesh implementations, and container security strategies. Organizations adopting cloud-native patterns must ensure XML Security controls function effectively in distributed, dynamically-scaled environments. As software supply chain attacks continue increasing in sophistication and frequency, protecting XML-based components becomes more critical to preventing compromise through build systems, package managers, and configuration mechanisms.
Successful XML Security programs require ongoing attention as new vulnerabilities emerge, parsing libraries evolve, and attack techniques become more sophisticated. Teams should maintain current knowledge of XML Security best practices, regularly update dependencies, and continuously test security controls effectiveness. By treating XML Security as an integral part of application security and supply chain protection rather than a niche technical concern, organizations can significantly reduce their attack surface and strengthen overall security posture in ways that protect both legacy systems and modern architectures.
For DevSecOps leaders seeking to enhance their software supply chain security posture with comprehensive XML Security and broader protection strategies, schedule a demo with Kusari to explore how advanced supply chain security platforms can help your team identify vulnerabilities, enforce security policies, and maintain visibility across your development pipeline while addressing XML Security concerns alongside other critical protection requirements.
Frequently Asked Questions About XML Security
What makes XML Security different from general application security?
XML Security differs from general application security due to the specific characteristics of XML as both a data format and processing mechanism. XML Security must address unique vulnerabilities that arise from XML parsers, entity expansion mechanisms, and the structural flexibility of markup languages. While general application security focuses on broad concerns like authentication and authorization, XML Security specifically tackles threats like XML External Entity attacks, entity expansion denial of service, and XML injection that don't apply to other data formats. The discipline also encompasses specialized technologies like XML Signature and XML Encryption that provide cryptographic protection tailored to XML's hierarchical structure.
How do XXE vulnerabilities occur in XML processing?
XXE vulnerabilities occur in XML processing when parsers are configured to resolve external entity references without proper restrictions. XML's Document Type Definition (DTD) feature allows documents to define entities that reference external resources using URLs or file paths. When an application parses a malicious XML document containing external entity declarations, the parser may attempt to retrieve and incorporate those external resources. Attackers exploit this behavior to read local files, scan internal networks, cause denial of service, or perform server-side request forgery attacks. XXE vulnerabilities typically arise from default parser configurations that enable external entity processing, lack of input validation, and insufficient awareness of XML's entity expansion capabilities.
What are the key components of implementing XML Signature correctly?
Implementing XML Signature correctly requires several key components working together. Teams must select appropriate signature algorithms based on security requirements and compatibility needs, ensuring deprecated algorithms like SHA-1 are avoided. Proper canonicalization configuration ensures signatures remain valid across different processing environments that might normalize whitespace or attribute ordering differently. The implementation must correctly specify which document elements are being signed through reference elements, and signature verification must validate that the actual processed content matches the signed references to prevent signature wrapping attacks. Key management infrastructure must securely store private signing keys and distribute public verification keys reliably. Teams should also implement proper error handling that fails securely when signature verification fails rather than proceeding with untrusted content.
Can XML Security controls impact application performance significantly?
XML Security controls can impact application performance, but the magnitude depends on implementation approaches and workload characteristics. Schema validation adds parsing overhead, particularly for complex schemas or large documents. XML Signature creation and verification involves cryptographic operations that consume CPU resources, with impact varying based on document size, signature algorithms, and hardware capabilities. XML Encryption similarly requires computational resources for encryption and decryption operations. Performance impacts can be mitigated through various optimization strategies including caching compiled schemas, using hardware cryptographic acceleration, selecting efficient algorithms appropriate for the threat model, implementing streaming parsers for large documents, and applying security controls selectively based on risk assessment. Teams should benchmark their specific workloads to quantify performance impacts and determine acceptable trade-offs between security and efficiency.
How should teams handle XML Security in legacy applications?
Handling XML Security in legacy applications requires a phased approach that balances risk reduction with practical constraints. Teams should start by inventorying all XML processing points within legacy systems, identifying parser libraries, configuration settings, and data flows. Updating parser configurations to disable external entity processing and limit resource consumption often provides significant security improvement with minimal code changes. When parser libraries contain known vulnerabilities, teams should prioritize updating to patched versions, testing thoroughly to identify compatibility issues. For applications where code modification is difficult, teams can implement security controls at network boundaries using XML gateways or firewalls that validate and sanitize XML traffic. Runtime application self-protection tools can provide detection and blocking capabilities for legacy applications where source code modification isn't feasible. Risk-based prioritization should focus remediation efforts on externally-facing systems and those processing sensitive data.
What testing approaches effectively identify XML Security vulnerabilities?
Effective XML Security testing combines multiple approaches addressing different vulnerability types and development stages. Static application security testing analyzes source code to identify insecure parser configurations, XML injection risks, and improper signature verification implementations. Dynamic application security testing probes running applications with malicious XML payloads including XXE exploitation attempts, entity expansion attacks, and injection vectors. Fuzzing generates malformed and unexpected XML inputs to identify parser crashes and resource exhaustion conditions. Manual penetration testing evaluates complex vulnerabilities like signature wrapping attacks that automated tools may miss. Unit tests should verify that parser configurations properly block known attack patterns, while integration tests validate end-to-end security controls including encryption and signature verification. Teams should maintain libraries of test cases covering common XML attack patterns and regularly update test suites as new vulnerabilities emerge.
Does the shift to JSON and other formats eliminate XML Security concerns?
The shift to JSON and other formats does not eliminate XML Security concerns for most enterprise organizations. XML remains deeply embedded in enterprise systems, particularly in legacy applications, SOAP-based web services, configuration management, build systems, and integration with partner organizations using established XML-based protocols. Many regulatory compliance frameworks and industry standards continue to mandate XML formats for specific use cases. Organizations typically operate hybrid environments where both XML and newer formats coexist, requiring teams to maintain XML Security expertise alongside security knowledge for alternative formats. The software supply chain heavily utilizes XML in build manifests, deployment descriptors, and package metadata regardless of what data formats applications use at runtime. Rather than replacing XML entirely, most organizations must secure multiple data formats simultaneously, making XML Security knowledge remain valuable for DevSecOps teams.
What role does XML Security play in API security strategies?
XML Security plays an important role in API security strategies, particularly for organizations operating SOAP-based services or REST APIs that accept XML payloads. API gateways should enforce XML Security controls including schema validation to ensure incoming requests conform to expected structures, blocking malformed or suspicious documents before they reach backend services. WS-Security implementations provide message-level security for SOAP APIs, enabling authentication, integrity protection, and confidentiality independent of transport layer security. For REST APIs accepting XML, security controls must validate content types, enforce size limits, and sanitize inputs to prevent XML injection attacks. API security strategies should implement defense-in-depth by combining perimeter controls at gateways with application-level validation and secure processing practices. Monitoring and logging of XML-related security events helps teams detect exploitation attempts and suspicious patterns that may indicate reconnaissance or attack activity.
How does containerization affect XML Security implementations?
Containerization affects XML Security implementations in several ways that teams must address. Container images must include XML parser libraries configured with secure defaults, and teams should scan images for vulnerable library versions as part of continuous integration pipelines. Security contexts for containers should apply the principle of least privilege, limiting filesystem access and network capabilities to reduce the impact of potential XXE exploitation. Container orchestration platforms like Kubernetes can enforce network policies that restrict which services can communicate, limiting the damage from server-side request forgery attacks through XXE vulnerabilities. Immutable infrastructure patterns where containers include baked-in configurations reduce the risk of XML configuration tampering at runtime. Service mesh technologies can provide centralized XML validation and security policy enforcement across microservices. Container security scanning should specifically check for insecure XML parser configurations and known vulnerabilities in XML processing libraries included in images.
What key management practices support XML Signature and Encryption?
Effective key management practices for XML Signature and Encryption start with secure key generation using cryptographically strong random number generators and appropriate key lengths. Keys should be stored in dedicated key management systems, hardware security modules, or cloud-based key management services rather than in application code or configuration files. Access controls must restrict which systems and users can access signing and encryption keys, with separation between keys used for different purposes. Regular key rotation schedules reduce the window of exposure if keys become compromised. Key distribution mechanisms must ensure that verification and decryption keys reach authorized recipients securely without exposing private signing or encryption keys. Organizations should implement key lifecycle management covering creation, active use, rotation, archival, and destruction phases. Audit logging should track all key usage for compliance and incident investigation purposes. Disaster recovery procedures must address key backup and recovery while maintaining security guarantees.
