Granular Access
Understanding Granular Access: Fine-Tuned Permission Control for Software Supply Chain Security
Granular access represents a security paradigm that enables organizations to define and enforce highly specific, attribute-based permissions for users, systems, and services interacting with software artifacts, infrastructure, and development resources. Rather than applying broad, role-based permissions that grant sweeping access to entire systems or datasets, granular access allows security teams to control access at the individual resource, operation, or even data field level. This fine-tuned approach is particularly critical in software supply chain security, where unauthorized access to build systems, artifact repositories, or signing keys can compromise the integrity of software delivered to end users.
This concept matters most to DevSecOps leaders, security architects, platform engineers, and CISOs responsible for protecting software development and delivery pipelines. These practitioners implement granular access controls when designing secure CI/CD systems, managing artifact repositories, controlling access to cryptographic materials, and enforcing least-privilege principles across development infrastructure. The challenge extends beyond traditional application security into the complex web of build systems, dependency repositories, container registries, and deployment platforms that constitute the modern software supply chain.
Understanding and implementing granular access controls delivers measurable security outcomes: reduced blast radius from compromised credentials, improved audit trails for compliance requirements, prevention of unauthorized modifications to critical software artifacts, and alignment with frameworks like SLSA (Supply-chain Levels for Software Artifacts) that require authenticated and authorized build processes. As software supply chain attacks increase in sophistication—from dependency confusion to compromised build systems—the ability to control access with precision has shifted from a best practice to a fundamental security requirement.
What is Granular Access in Software Supply Chain Security?
Granular access control refers to the implementation of authorization mechanisms that operate at a fine level of detail, allowing organizations to specify exactly who or what can perform specific actions on particular resources under defined conditions. In the context of software supply chain security, this means controlling access not just to systems or repositories as a whole, but to individual artifacts, specific operations (read, write, delete, sign), particular branches or tags in version control, individual secrets or keys, and even specific fields within metadata or attestations.
Traditional access control models often rely on coarse-grained permissions. A developer might have "write access" to an entire repository, a service account might have "admin privileges" on a container registry, or a build system might have unrestricted access to all signing keys. These broad permissions create security gaps. A compromised developer account could modify any code in the repository. A breached service account could replace legitimate container images with malicious versions. A vulnerable build system could sign arbitrary artifacts with production keys.
Granular access addresses these risks by breaking permissions down into their smallest meaningful units. Instead of repository-wide write access, a developer receives permission to merge pull requests only to specific branches after code review approval. Rather than registry-wide admin access, a service account gains permission only to push images with specific tags to designated namespaces. Build systems receive time-limited, audit-logged access to sign artifacts only for specific projects and only after successful completion of required security checks.
This approach aligns with the principle of least privilege, which states that users and systems should have only the minimum permissions necessary to perform their legitimate functions. In software supply chains, where a single compromised component can cascade through countless downstream consumers, implementing least privilege through granular access becomes a critical defense layer. The approach requires more upfront design work and ongoing management but dramatically reduces the potential damage from breached credentials, insider threats, or compromised systems.
How Granular Access Control Works in Practice
Implementing granular access in software supply chain environments involves several interconnected components working together to evaluate and enforce fine-grained permissions. At the foundation sits an identity and authentication layer that establishes who or what is requesting access. This identity might represent a human developer, a CI/CD pipeline, a container orchestration system, or an automated security scanner.
Once identity is established, the authorization layer evaluates the request against a detailed policy framework. Unlike simple role-based access control (RBAC) where a user's role determines all permissions, granular access typically employs attribute-based access control (ABAC) or policy-based access control (PBAC). These models evaluate multiple attributes simultaneously: the requester's identity and group memberships, the specific resource being accessed, the operation being requested, environmental context (time of day, network location, device security posture), and the current state of the resource (locked for release, under review, flagged by security scanning).
Consider a practical example in a container registry. A deployment system requests access to pull a container image tagged "production" from a specific namespace. The granular access system evaluates multiple factors:
- Identity verification: Is this request coming from the authenticated deployment service?
- Resource permission: Does this service have pull permissions for this specific namespace and image?
- Tag restrictions: Is the service authorized to pull production-tagged images, or only development tags?
- Time-based constraints: Is this access occurring during an approved deployment window?
- Attestation requirements: Does the requested image include required security attestations and SBOM data?
- Vulnerability status: Has this image passed vulnerability scanning with acceptable risk thresholds?
Only when all conditions are satisfied does the access request succeed. If the same deployment system requested access to push a new image or delete an existing one, different policies would apply with potentially different outcomes. This multi-dimensional evaluation enables security teams to craft sophisticated permission models that reflect actual security requirements rather than settling for overly permissive access due to limited control options.
The enforcement mechanism varies by platform but typically occurs at API gateways, repository proxies, or within the platforms themselves. Modern software supply chain security platforms integrate with existing authentication providers (OAuth, OIDC, SAML) and authorization systems while adding supply-chain-specific policy capabilities. These systems maintain detailed audit logs of all access decisions, creating accountability and supporting forensic investigation when security incidents occur.
Why Granular Access Matters for Software Supply Chain Security
The software supply chain has emerged as a primary attack vector for sophisticated threat actors precisely because it offers high-value targets with historically weak access controls. When attackers compromise a developer's credentials, they don't just gain access to source code—they potentially access build systems, signing infrastructure, deployment pipelines, and distribution channels. A single breach can affect thousands or millions of downstream users who trust the compromised software supplier.
Recent high-profile supply chain attacks demonstrate this pattern repeatedly. Attackers compromise credentials with excessive permissions, move laterally through systems with inadequate access segmentation, and ultimately inject malicious code or artifacts that propagate through the supply chain. Granular access control directly addresses these attack patterns by limiting what compromised credentials can accomplish.
When access is granular, a compromised developer account cannot automatically push code to protected branches or trigger production builds. Stolen service account credentials cannot access resources outside their narrowly defined scope. A vulnerable build agent cannot access signing keys for projects it shouldn't be building. Each of these limitations reduces the blast radius of a security incident, giving defenders time to detect and respond before irreversible damage occurs.
Beyond breach containment, granular access supports several other critical security objectives in software supply chains:
Compliance and auditability: Regulations and frameworks increasingly require organizations to demonstrate who accessed what resources and when. Granular access systems generate detailed audit trails at the specific operation level, making compliance audits more straightforward and providing evidence of proper security controls. Frameworks like SLSA Level 3 and 4 explicitly require authenticated and authorized build processes with clear provenance, which granular access enables.
Separation of duties: Security best practices dictate that critical operations should require multiple parties or approval stages. Granular access makes separation of duties practical by allowing organizations to require, for example, that code commits and code reviews must come from different individuals, or that production deployments require both automated security checks and manual approval from authorized personnel.
Temporal and contextual security: Software development isn't static. A build system might need access to signing keys during active builds but not otherwise. A developer might need elevated permissions during an approved maintenance window but not at other times. Granular access enables time-based, context-aware permissions that automatically adapt to changing circumstances without manual intervention.
Third-party and contractor risk management: Modern development teams include internal employees, external contractors, partner organizations, and automated systems. Granular access allows security teams to provide each party with precisely the access needed for their role while preventing access to sensitive resources outside their scope. When contracts end or partnerships change, removing granular permissions is more targeted and less likely to disrupt unrelated workflows.
And there's a practical business benefit beyond security: granular access reduces friction in collaborative environments. When developers have confidence that permissions are precisely scoped, they're more willing to grant necessary access. Security teams spend less time investigating false alarms from overly broad permissions triggering on legitimate but unexpected access patterns. Platform engineers can design systems with clear security boundaries that remain flexible as organizational needs evolve.
Implementing Granular Access: Key Considerations and Best Practices
Transitioning from coarse-grained to granular access control requires thoughtful planning and phased implementation. Organizations that attempt to implement perfectly granular permissions overnight typically create more problems than they solve, with legitimate workflows breaking and productivity grinding to a halt. A more effective approach begins with identifying high-value assets and high-risk access patterns, then incrementally increasing access control granularity.
Start with asset classification: Not all resources require the same level of access control granularity. Signing keys for production releases demand more granular control than development environment configuration files. Container images destined for customer deployment need stricter access rules than internal testing images. Begin by classifying assets based on their security impact if compromised, their compliance requirements, and their position in the software supply chain. Focus initial granular access implementation on the highest-priority assets.
Map current access patterns: Before implementing restrictive policies, understand how developers, systems, and services currently access resources. Many organizations discover that actual access patterns differ significantly from what they assumed. This mapping phase identifies legitimate workflows that must continue functioning, overly permissive access that can be immediately restricted, and unusual access patterns that warrant investigation. Implement monitoring and logging before enforcement to gather this data without disrupting operations.
Design policies around workflows, not individuals: Effective granular access policies define permissions based on what someone is trying to accomplish rather than who they are. "Deploy to staging environment" represents a workflow that might require accessing specific branches, container registries, and deployment credentials. Different individuals might legitimately perform this workflow, and the workflow itself might be triggered by automation. Defining access at the workflow level creates consistency and makes permission management more scalable than individually managing each person's access.
Implement progressive authorization: Some sensitive operations benefit from requiring multiple factors or approval stages. For example, pushing code to a repository might require only authentication, but merging to a protected branch requires code review approval, and tagging a release requires both automated security scanning and approval from a release manager. Granular access systems can enforce these progressive authorization requirements, embedding security checkpoints directly into development workflows.
Maintain clear audit trails: One of the primary benefits of granular access is detailed visibility into who did what and when. This requires robust logging that captures not just successful access but also denied attempts, the policies that were evaluated, and the context that influenced access decisions. These logs serve multiple purposes: security monitoring and incident response, compliance auditing, troubleshooting access issues, and refining policies based on actual usage patterns.
Plan for break-glass scenarios: Even with well-designed granular access, emergencies occur that require rapid access outside normal permissions. Perhaps a critical vulnerability requires immediate patching across all repositories, or a production incident demands access to resources usually restricted. Implement documented break-glass procedures that provide emergency access while maintaining audit trails and triggering appropriate alerts. Break-glass access should be time-limited, automatically revoked after use, and subject to mandatory review.
Integrate with existing identity systems: Granular access should build on existing authentication and identity infrastructure rather than creating parallel systems. Integrate with enterprise identity providers, leverage existing group memberships and attributes, and synchronize with HR systems to automatically adjust access when roles change. This integration reduces administrative overhead and ensures granular access policies stay aligned with organizational changes.
Common Challenges and Limitations of Granular Access
While granular access provides significant security benefits, implementation comes with real challenges that organizations should anticipate and plan for. Understanding these limitations helps set realistic expectations and guides investment in supporting infrastructure and processes.
Increased complexity: Granular access policies are inherently more complex than coarse-grained alternatives. Managing permissions at the individual resource and operation level means many more policies to define, test, and maintain. This complexity can lead to configuration errors where legitimate access is inadvertently blocked or, worse, where gaps in policies allow unintended access. Organizations need robust policy testing frameworks, clear documentation, and ideally policy-as-code practices that enable version control and review of access rules.
Performance considerations: Evaluating detailed access policies on every request introduces latency. When a CI/CD pipeline makes hundreds or thousands of API calls during a build, evaluating complex attribute-based policies for each call can add noticeable overhead. This requires careful architectural decisions: caching authorization decisions where appropriate, pre-computing permissions for common scenarios, and optimizing policy evaluation engines. Organizations must balance security granularity against performance requirements, potentially using coarser policies for high-volume, low-risk operations while reserving detailed evaluation for sensitive resources.
User experience friction: Developers accustomed to broad access may experience frustration when granular policies block actions they consider legitimate. "Access Denied" errors during active development interrupt flow and reduce productivity. Managing this friction requires several approaches: clear error messages that explain why access was denied and how to request appropriate permissions, self-service mechanisms for requesting temporary elevated access, and ongoing communication about security requirements. The goal is making security boundaries clear without making them obstructive.
Initial implementation effort: Moving from simple role-based access to granular control requires significant upfront investment. Teams must classify resources, define policies, configure enforcement mechanisms, update workflows to accommodate new approval processes, and train users on changed procedures. This implementation burden often competes with feature development and other priorities. Successful implementations typically phase the rollout, starting with highest-risk areas and gradually expanding coverage rather than attempting complete implementation simultaneously.
Policy drift and maintenance: Software supply chains evolve constantly—new repositories are created, services are added, team structures change, and workflows adapt. Granular access policies must evolve in sync with these changes or they become outdated. Outdated policies either block legitimate new workflows (forcing users to work around security controls) or fail to protect new resources (leaving security gaps). Preventing policy drift requires treating access policies as code with the same discipline applied to application code: version control, automated testing, regular review, and clear ownership.
Tool fragmentation: Software supply chains span numerous platforms: version control systems, artifact repositories, container registries, build systems, deployment platforms, and cloud infrastructure. Each platform has its own access control mechanisms with different capabilities, terminologies, and configuration approaches. Implementing consistent granular access across this fragmented landscape is challenging. Organizations either accept inconsistency across platforms or invest in unified policy management layers that translate organizational security requirements into platform-specific configurations.
Granular Access in the Context of DevSecOps and CI/CD Security
DevSecOps practices aim to integrate security throughout the software development lifecycle rather than treating it as a final gate before release. Granular access control is fundamental to this integration, enabling security requirements to be enforced continuously without blocking development velocity. In CI/CD pipelines, where automation moves code from development through testing to production, granular access ensures that each stage can access only the resources it legitimately needs.
Consider a typical CI/CD pipeline progressing through multiple stages: source code checkout, dependency resolution, compilation, testing, security scanning, artifact building, signing, and deployment. Each stage requires access to different resources and should have different permission levels:
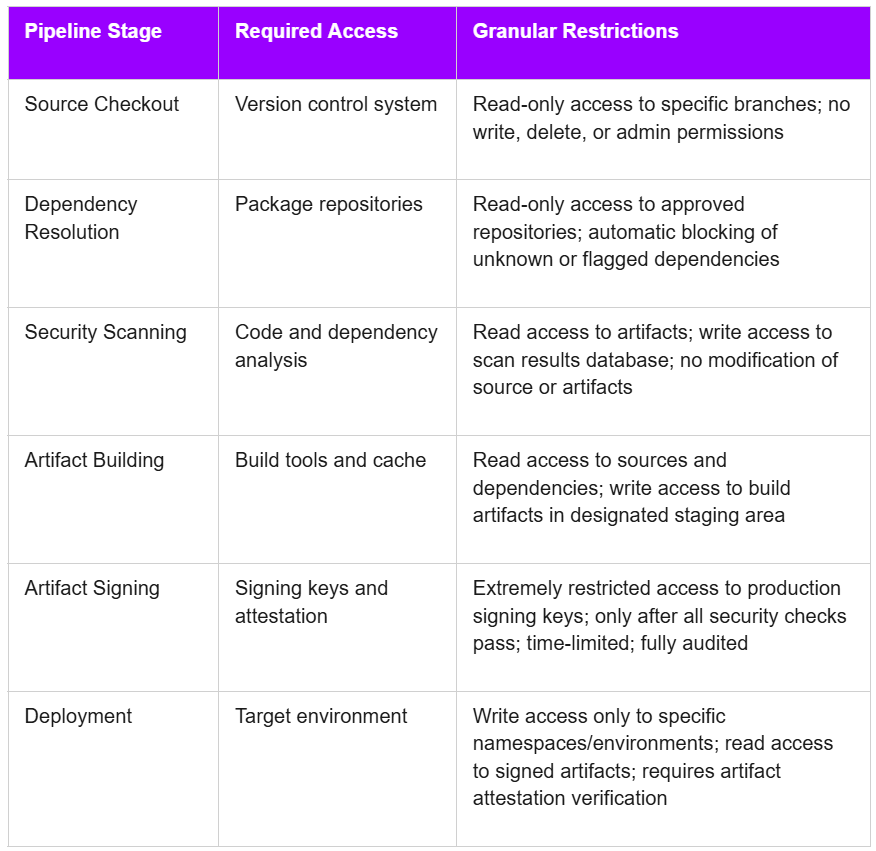
This staged access model prevents compromise at one pipeline stage from cascading to others. A vulnerability in the testing framework cannot compromise production signing keys. A compromised dependency scanning tool cannot modify source code or push malicious artifacts. Each pipeline component operates within a security boundary defined by granular access policies.
Modern CI/CD security also requires protecting the pipeline infrastructure itself. Build agents, runner systems, and orchestration platforms need access to credentials, keys, and sensitive configuration. Granular access ensures that each build agent can access only the secrets needed for its assigned projects, that runners in less-trusted environments have more restricted access than those in hardened infrastructure, and that orchestration platforms can manage workflows without having direct access to the sensitive resources those workflows use.
Integration with attestation and provenance tracking creates additional opportunities for granular access. Systems can require that artifacts include valid attestations before allowing access, ensuring that only properly built and verified software progresses through the supply chain. Access policies can verify that the provenance metadata matches expected patterns—for example, that production deployments come only from artifacts built by authorized CI systems from specific source repositories with required approvals. This binds granular access control to the broader secure SDLC framework, creating multiple reinforcing security layers.
Granular Access and Software Supply Chain Security Frameworks
Industry frameworks and standards increasingly emphasize fine-grained access control as a core requirement for secure software supply chains. The SLSA framework, developed by the Open Source Security Foundation and widely adopted across the industry, explicitly addresses access control at multiple levels. SLSA Level 2 requires that build processes are documented and use version control, implicitly requiring some access control. SLSA Level 3 and Level 4 require that builds are hardened with authenticated actors and isolated execution, which demands granular access to ensure only authorized systems and individuals can trigger builds, access signing keys, and publish artifacts.
The software supply chain security platform approach recognizes that meeting these framework requirements requires unified visibility and control across fragmented tooling. Organizations implementing SLSA attestations need granular access to ensure that only compliant build systems can generate valid attestations and that consumers can verify attestations before accepting artifacts.
Similarly, emerging regulations around software security—including the U.S. Executive Order on Improving the Nation's Cybersecurity and related NIST guidance—emphasize supply chain security practices that depend on granular access. Requirements for SBOM (Software Bill of Materials) generation and distribution presume that organizations control who can create, modify, and access these critical metadata documents. Provenance attestations must be protected from tampering, requiring fine-grained access to signing infrastructure. Vulnerability disclosure workflows need granular permissions to ensure sensitive vulnerability information is shared with appropriate parties while being protected from premature public disclosure.
The concept of "verifiable builds" central to supply chain security frameworks depends on granular access at multiple levels. For a build to be truly verifiable, the build environment must be trustworthy, which means access to that environment must be strictly controlled. The source code being built must be from a verified source with proper access controls preventing unauthorized modification. Dependencies must come from approved sources with granular policies preventing dependency confusion or substitution attacks. And the resulting artifacts must be signed with protected keys that only authorized build systems can access under specific conditions.
Tooling and Technology for Implementing Granular Access
Implementing granular access in software supply chains requires leveraging appropriate technologies and platforms. Modern approaches typically combine several complementary technologies working together.
Identity and Access Management (IAM) platforms: Enterprise IAM systems provide foundational identity services—authentication, single sign-on, multi-factor authentication, and directory services. Leading platforms include Okta, Azure Active Directory, Google Cloud Identity, and open-source solutions like Keycloak. These systems establish user and service identities that granular access policies build upon. They increasingly support fine-grained authorization capabilities, though supply-chain-specific use cases often require additional layers.
Policy engines and frameworks: Dedicated policy engines evaluate complex authorization decisions based on multiple attributes. Open Policy Agent (OPA) has emerged as a popular open-source option, providing a flexible policy language and integration points with numerous platforms. Cloud providers offer their own policy services (AWS IAM, Azure RBAC with conditions, Google Cloud IAM with conditions) that provide increasingly granular capabilities. These engines evaluate policies written in declarative languages, enabling security teams to define sophisticated access rules without custom code.
Attribute-based access control systems: ABAC systems extend beyond simple role assignments to evaluate multiple attributes when making access decisions. These might include user attributes (department, clearance level, employment type), resource attributes (classification, owner, lifecycle stage), environmental attributes (time, location, device posture), and contextual attributes (recent authentication, risk score). Modern ABAC implementations integrate with IAM platforms and policy engines to provide flexible, fine-grained access control.
Platform-specific access controls: Most software supply chain platforms offer native access control capabilities with varying levels of granularity. GitHub provides repository permissions, branch protection rules, and environment protection rules. GitLab offers project-level permissions with custom roles. Container registries like Docker Hub, Google Container Registry, and Amazon ECR support namespace-level and tag-level permissions. Artifact repositories like Artifactory and Nexus provide fine-grained access to specific packages and versions. Effective granular access implementations leverage these native capabilities where they provide sufficient control while adding policy layers where they don't.
Service mesh and API gateway authorization: In containerized and microservice environments, service meshes (Istio, Linkerd) and API gateways (Kong, Ambassador) provide enforcement points for access policies. These technologies can evaluate and enforce access rules at the network level, controlling which services can communicate and which operations they can perform. This complements application-level access control, creating defense in depth.
Secrets management platforms: Granular access to cryptographic keys, certificates, tokens, and other secrets requires specialized secrets management. HashiCorp Vault, AWS Secrets Manager, Azure Key Vault, and Google Secret Manager provide fine-grained access control to secrets with features like time-limited access, automatic rotation, and detailed audit logging. These platforms integrate with build systems and deployment pipelines to provide just-in-time secret access with automatic revocation.
Software supply chain security platforms: Dedicated platforms focused on software supply chain security integrate many of these capabilities with supply-chain-specific policy enforcement. These platforms understand artifacts, build processes, dependencies, attestations, and provenance. They provide unified visibility and control across the fragmented tooling landscape, translating organizational security policies into platform-specific configurations and enforcement points. Organizations exploring software supply chain security often find that dedicated platforms reduce complexity compared to integrating numerous point solutions.
The Relationship Between Granular Access and Zero Trust Architecture
Granular access control aligns closely with zero trust security principles, which assume that threats exist both outside and inside traditional network perimeters. Zero trust architecture operates on the principle of "never trust, always verify," requiring explicit verification for every access request regardless of where it originates. This philosophy naturally leads to granular access as an implementation mechanism.
In traditional perimeter-based security, resources inside the "trusted" network often had coarse-grained access controls. Once an attacker breached the perimeter, lateral movement was relatively easy because internal resources assumed trust based on network location. Zero trust eliminates this assumption by treating every access request as potentially hostile, verifying identity and authorization for each request, and granting only the minimum necessary access.
For software supply chains, zero trust means that build systems don't automatically trust requests from version control, deployment systems don't automatically trust artifacts from build systems, and production environments don't automatically trust deployment systems. Each interaction requires authentication, authorization against granular policies, and validation of security attributes like attestations and signatures. This creates multiple verification points where compromised components can be detected and contained before causing widespread damage.
Zero trust implementations in software supply chains also emphasize continuous verification rather than single-point authentication. A developer might authenticate at the beginning of their workday, but granular access policies continue evaluating context throughout that session. If suspicious access patterns emerge—unusual repositories accessed, unexpected times, anomalous volume—policies can require re-authentication or block access entirely. This continuous verification complements granular access by adding temporal and behavioral dimensions to security decisions.
Monitoring and Auditing Granular Access in Software Supply Chains
Implementing granular access creates vast amounts of audit data—every access decision, every policy evaluation, every approval workflow. This data is valuable only if organizations can effectively monitor it for security events and analyze it for compliance and optimization purposes. Effective monitoring requires thoughtful approaches to log collection, analysis, alerting, and retention.
Centralized logging: Access logs from distributed systems—version control, artifact repositories, build systems, deployment platforms—must aggregate in a centralized location for correlation and analysis. SIEM (Security Information and Event Management) platforms, log aggregation tools like Elasticsearch or Splunk, or cloud-native logging services provide this centralization. Logs should capture not just successful access but denied attempts, policy evaluation details, and contextual information that influenced decisions.
Real-time alerting: Certain access patterns warrant immediate investigation: repeated denied access attempts potentially indicating credential compromise or misconfiguration, access to highly sensitive resources like production signing keys, unusual access patterns deviating from established baselines, or privilege escalation attempts. Automated alerting on these patterns enables rapid response before incidents escalate. Alert rules should be tuned carefully to avoid alert fatigue while catching genuine threats.
Behavioral analysis: Traditional security monitoring looks for known bad patterns—unauthorized access attempts, malware signatures, known attack techniques. Granular access logs enable behavioral analysis that detects anomalies even when no specific rule is violated. Machine learning models can establish baselines for normal access patterns for each user and system, then flag deviations: a developer accessing repositories they've never touched before, a build system pulling dependencies from new sources, deployment patterns occurring at unusual times. These anomalies don't necessarily indicate compromise but warrant investigation.
Compliance reporting: Many regulatory frameworks require demonstrating who accessed what resources and when. Granular access logs provide the raw data for compliance reports, but effective compliance requires structuring and presenting this data appropriately. Regular reports should show: privileged access events, access to sensitive resources, changes to access policies, approval workflows for critical operations, and any access violations or policy exceptions. These reports serve both internal compliance teams and external auditors.
Policy effectiveness analysis: Beyond security monitoring, granular access logs reveal how well policies are working. Frequent denied access attempts might indicate overly restrictive policies that need adjustment or poor user training. Rarely used permissions might indicate over-provisioning that should be revoked. Access patterns that consistently bypass intended controls might reveal gaps in policy design. Regular analysis helps optimize the balance between security and productivity.
To see how Kusari helps organizations implement granular access control with unified visibility and policy enforcement across software supply chain tools, request a demo.
Frequently Asked Questions About Granular Access
What's the difference between granular access and role-based access control (RBAC)?
Role-based access control assigns permissions based on predefined roles (developer, admin, operator), with each role having a fixed set of permissions. Granular access goes beyond roles to evaluate multiple attributes—specific resources being accessed, particular operations being performed, contextual factors like time and location, and dynamic conditions like security scan results. While RBAC might give all developers write access to repositories, granular access can specify which repositories, which branches, under what conditions, and with what approval requirements. Granular access often uses attribute-based access control (ABAC) or policy-based access control (PBAC) as implementation mechanisms.
How does granular access improve software supply chain security specifically?
Software supply chain attacks often succeed because compromised credentials have overly broad permissions that enable lateral movement and persistent compromise. Granular access limits the blast radius of compromised credentials by restricting what those credentials can access. A compromised developer account cannot push to protected branches or access production signing keys. A breached build system cannot access resources outside its specific project scope. Granular access also enables verification of build provenance and attestations, ensures that only authorized systems can sign artifacts, and creates detailed audit trails for compliance and incident investigation—all critical requirements for supply chain security frameworks like SLSA.
What are the performance implications of implementing granular access control?
Evaluating detailed access policies on every request introduces some latency compared to simple permission checks. The impact depends on policy complexity, the number of attributes evaluated, and how frequently access checks occur. In CI/CD pipelines making thousands of API calls during builds, poorly optimized granular access can add noticeable overhead. Mitigation strategies include caching authorization decisions for short periods, pre-computing permissions for common scenarios, optimizing policy evaluation engines, and using coarser policies for high-volume low-risk operations while reserving detailed evaluation for sensitive resources. Most modern policy engines are optimized for performance, making the overhead acceptable for the security benefits gained.
How do you prevent granular access policies from becoming too complex to manage?
Policy complexity is a legitimate challenge that requires several management practices. Treat access policies as code with version control, automated testing, and review processes. Define policies based on workflows rather than individuals, creating reusable permission patterns. Implement policy hierarchies where general rules apply broadly and specific exceptions are clearly documented. Use policy-as-code tools that enable testing policies before deployment. Regularly review and prune unused policies. Maintain clear documentation explaining policy intent, not just technical implementation. And critically, start with high-value assets and expand granularity gradually rather than attempting comprehensive coverage immediately.
Can granular access work with open source software development where contributors come from outside the organization?
Yes, granular access is particularly valuable for open source projects with diverse contributors. External contributors can have read access to source code and permission to submit pull requests without having any direct write access to repositories. Granular policies can require that external contributions go through mandatory review by trusted maintainers before merging. Signing keys for release artifacts remain accessible only to core maintainers, preventing external contributors from publishing malicious releases even if they contribute code. Many platforms like GitHub support fine-grained permissions for open source projects, enabling maintainers to collaborate with global contributors while maintaining security boundaries for critical operations.
How does granular access integrate with existing identity providers and SSO systems?
Modern granular access implementations integrate with enterprise identity providers through standard protocols like SAML, OAuth 2.0, and OpenID Connect. The identity provider handles authentication and provides user attributes (group memberships, department, role), which granular access systems use when evaluating policies. This integration means users maintain a single identity and authentication experience while gaining access to multiple systems, each enforcing its own granular policies based on that identity. Service accounts and automation also leverage these integration points, often using OAuth client credentials or workload identity mechanisms to establish machine identities that granular access policies can evaluate.
Building Effective Granular Access Into Your Security Strategy
As software supply chain security moves from emerging concern to critical business requirement, the ability to control access with precision becomes non-negotiable. Granular access provides the foundation for implementing least privilege principles, meeting framework requirements like SLSA, maintaining compliance with evolving regulations, and containing the blast radius when security incidents occur. Organizations that continue relying on coarse-grained permissions face increasing risk as attackers specifically target supply chain weaknesses created by overly permissive access.
The path to effective granular access begins with understanding current access patterns and identifying high-value assets that demand protection. Rather than attempting to implement perfect granularity everywhere immediately, focus on incremental improvement starting with the most critical resources—production signing keys, protected branches in critical repositories, artifact promotion to production environments, and access to secrets and credentials. Each increment provides measurable security improvement while building organizational capability and experience with granular access implementation.
Success requires treating access policies as first-class artifacts in your infrastructure-as-code and security-as-code practices. Version control, automated testing, peer review, and clear ownership should apply to access policies with the same rigor applied to application code. This discipline prevents policy drift, enables collaboration between security and development teams, and creates accountability for access decisions. The investment in policy management infrastructure pays dividends in reduced security incidents, faster compliance audits, and confidence that access controls remain effective as systems evolve.
Granular access control represents a fundamental shift from perimeter-based security to zero trust principles applied throughout the software supply chain. By verifying every access request against detailed policies considering identity, resource, operation, and context, organizations create multiple defensive layers that prevent single compromises from cascading into widespread breaches. Combined with attestation, provenance tracking, and continuous security monitoring, granular access forms the control plane for modern software supply chain security, enabling organizations to innovate rapidly while maintaining the security and compliance posture required.
