Security that sees the full software supply chain
Turn your SBOMs and vulnerability noise into a live map with actionable insights so you can ship secure software fast. Get software supply chain management you can trust.
VULNERABILITY
Critical
Low
1.9
VULNERABILITY
Critical
Low
2.0


VULNERABILITY
Critical
Low
1.75


VULNERABILITY
Critical
Moderate
4.32

VULNERABILITY
Critical
Low
3.14


VULNERABILITY
Critical
Critical
5.02

VULNERABILITY
Critical
Moderate
4.83


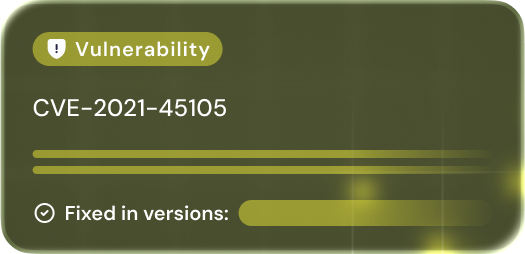

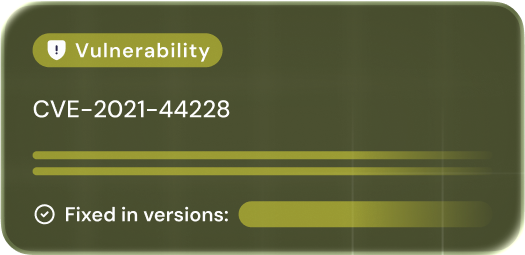
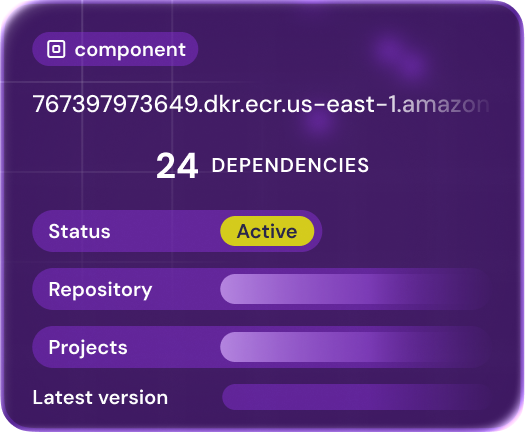
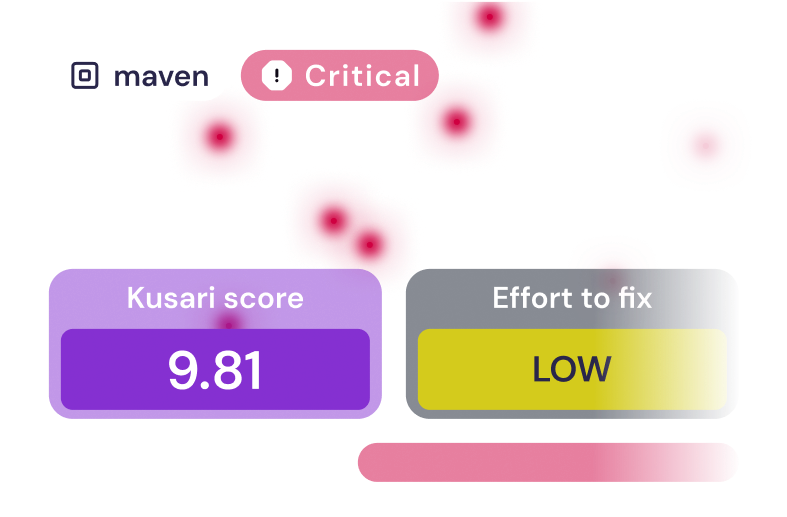
VULNERABILITY
Critical
Critical
9.81
VULNERABILITY
Critical
Moderate
4.71


VULNERABILITY
Critical
Moderate
4.92

VULNERABILITY
Critical
Moderate
5.96


VULNERABILITY
Critical
Low
1.86


VULNERABILITY
Critical
Low
1.32


VULNERABILITY
Critical
Critical
1.41


Scanners flood you with alerts and SBOMs only list what’s present.
Kusari tells you what you need to know.
What to fix
When it showed up
How it got there
Who can fix it fast
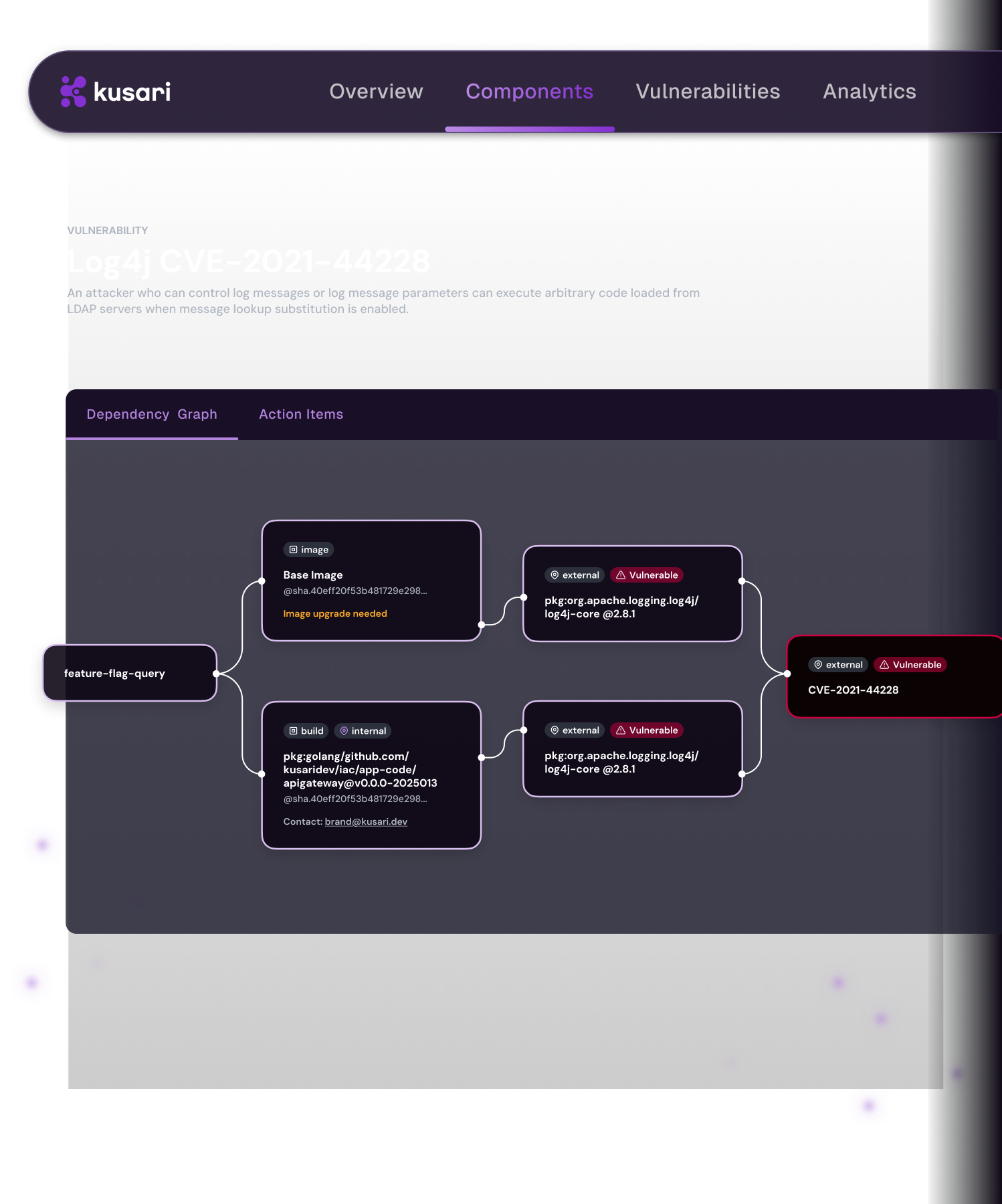
SOLUTION
SBOMs tell you what’s there, Kusari tells you what matters
Kusari continuously maps every component in your software. See where each component came from, what’s at risk, how to fix issues, and when to enforce policy. So when the critical vulnerability hits, you won’t waste time triaging 1,200 suspected issues—only the 5 that are real threats.
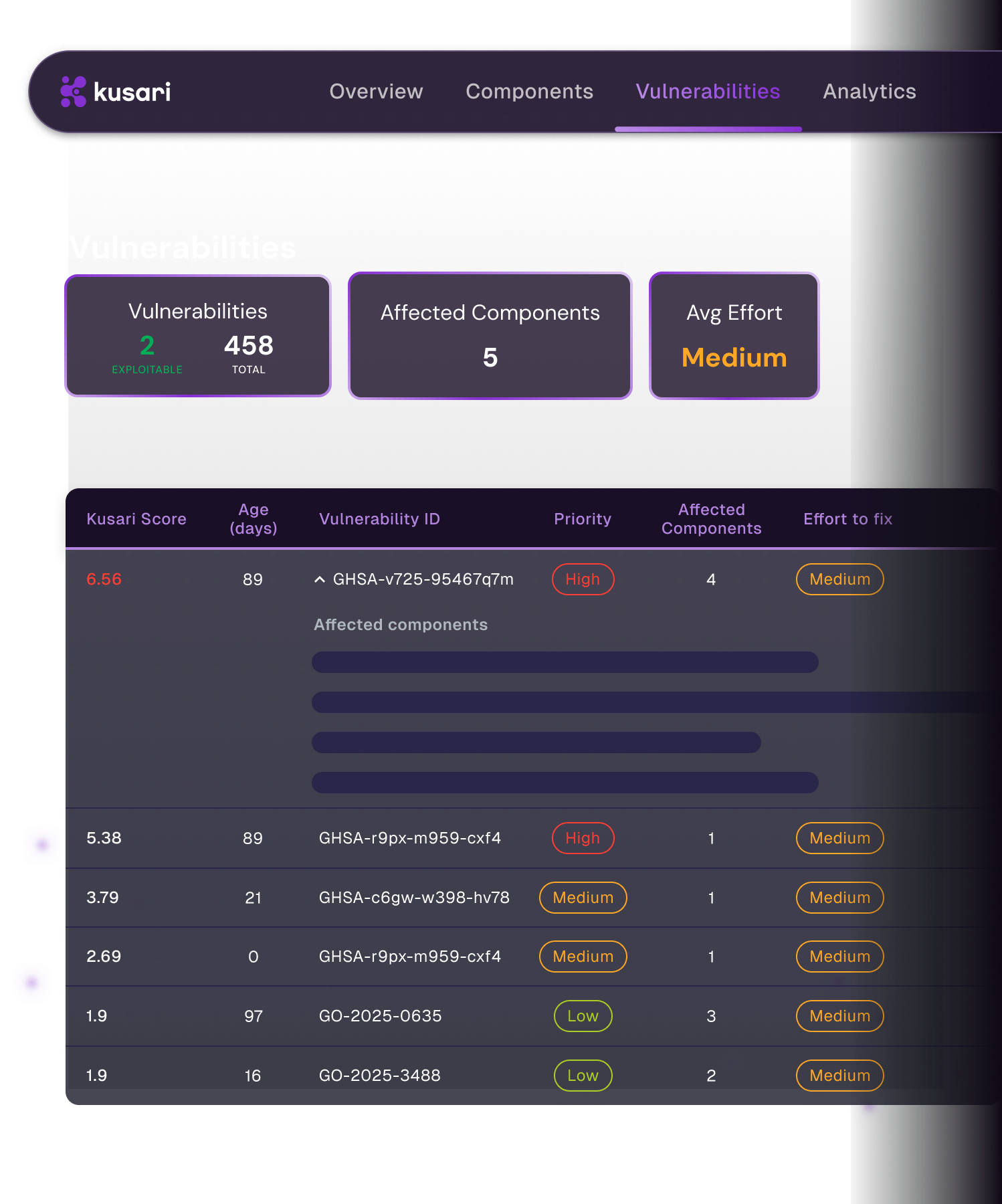
PROVENANCE
Fix the biggest threats fast
Trace each library, binary, and container back to its original source. No typosquatted packages or “mystery blobs” in your codebase—just a verifiable origin and history for everything you ship.
70% faster MTTR
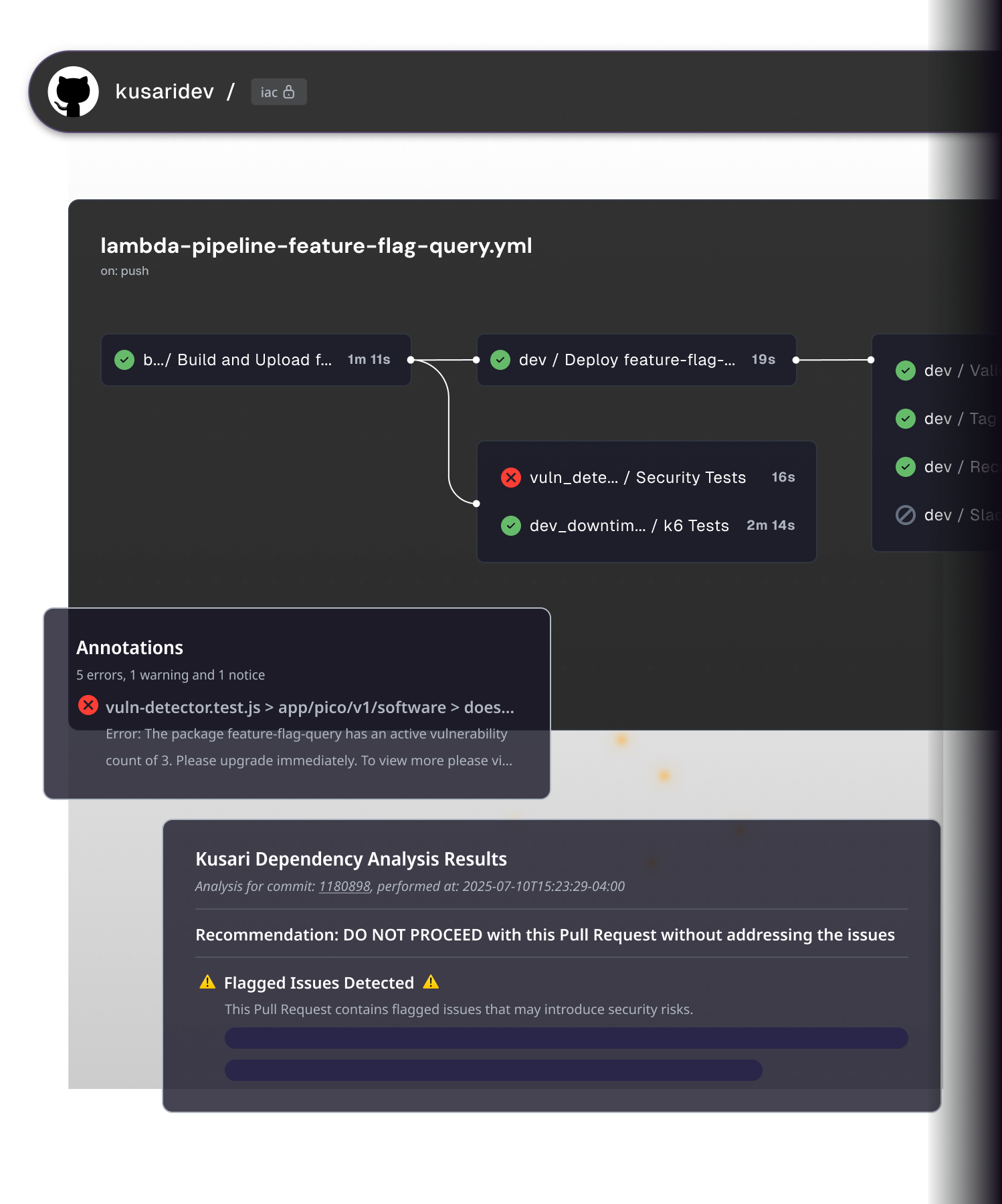
POLICY
Enforce what should—and shouldn’t—ship
Set automated rules to block insecure or unwanted components. Kusari acts as a guardian in your CI/CD where bad components trigger instant fail-fast build alerts, so only clean, approved code reaches production.
0 unknowns in prod
PROOF
Ship with evidence, not hope
Every build automatically produces a signed SBOM, vulnerability report (VEX), and provenance attestation. In minutes, you have an audit-ready packet to share with customers or regulators—tangible proof that your software supply chain management is secure and compliant.
Audit-ready in minutes
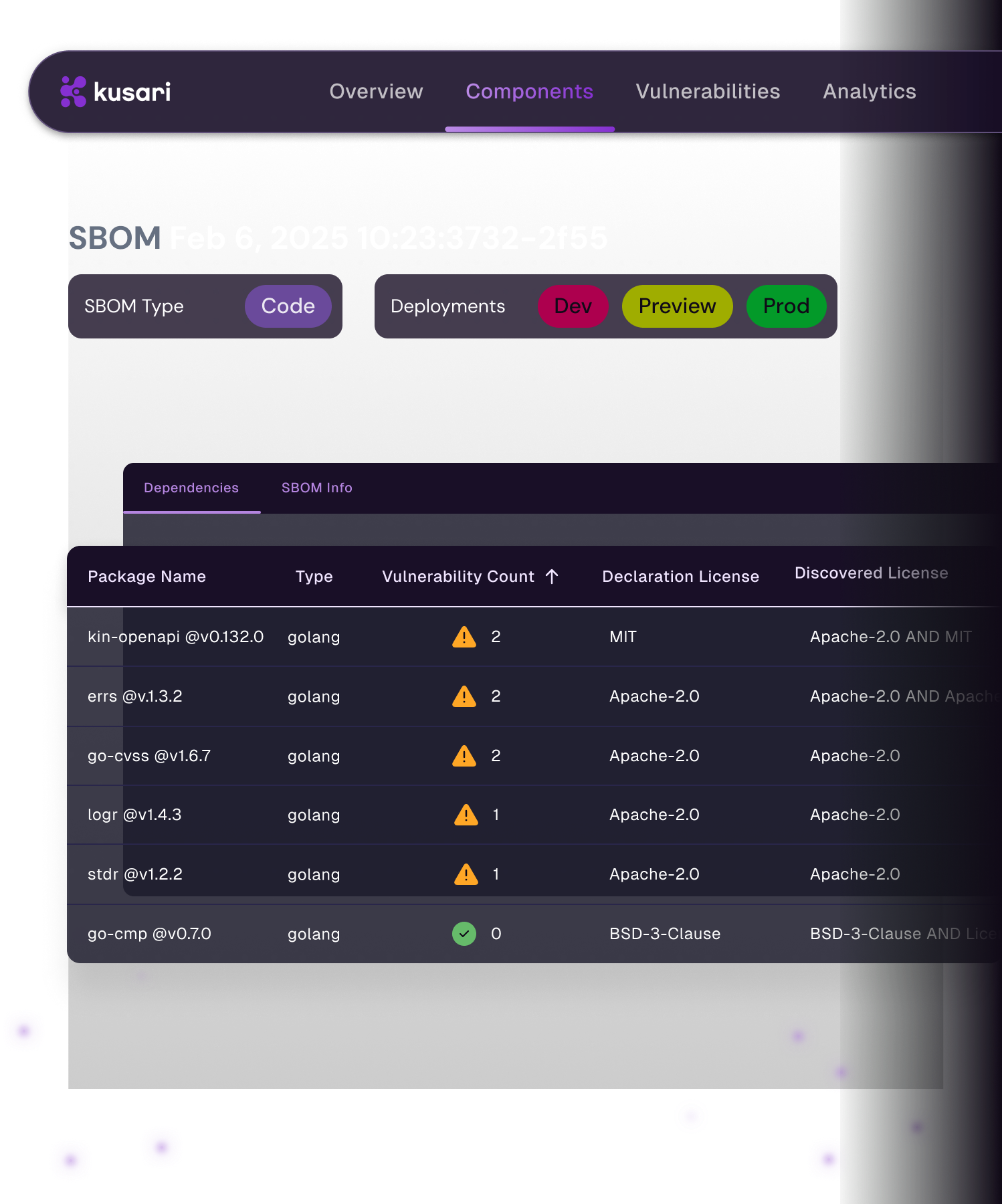
Answers for every team in the chain
Security
“Where is this CVE running?”
Kusari provides a real-time blast radius graph that shows every app/service affected.
Developer
“Is this dependency safe?”
Kusari provides a risk score for each dependency, checks for license issues and verifies provenance.
DevOps
“Can I trust this build?”
Kusari ensures every build includes a signed SBOM and passes all security policy checks in your CI pipeline before it can deploy.
Compliance
“Can we prove we’re secure?”
Kusari delivers an exportable report pack (SBOM, VEX, attestation) for each release.
For regulated industries

Protect patient data and comply with industry regulations. Secure every software dependency powering medical devices and other clinical systems.
Security Lead
Medical Device Company

Prevent malicious code from slipping into your mission-critical systems. Bring transparency and trust to every layer of your defense software stack.
Security Lead
Medical Device Company

Shield operational tech and infrastructure from online threats. Increase visibility and control with Kusari over the software components powering your utilities.
Security Lead
Medical Device Company

Protect your financial systems from the code up. Kusari secures your software supply chain to keep transaction and customer data safe.
Security Lead
Medical Device Company

We built Kusari to protect customers, but decided to test it on ourselves first. In 30 days, we cut our vulnerabilities by 87%, and our delivery pipeline is stronger than ever.
Tim Miller
CEO at Kusari
Leaders in open source
We believe open source development is a powerful driver of secure software. That’s why we started building GUAC and continue to contribute across open source projects daily.
Software supply chain management insights
All ResourcesShip secure software fast
Speak to one of our experts to gain the clarity, control, and confidence you need to ship secure software on schedule.






